Difference between revisions of "Virginia Tech Wifi"
imported>Waldrep (→Certificate Pinning) |
(Tag: Undo) |
||
| (34 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | On campus, there are 2 wireless networks: | |
| − | + | * '''eduroam''': uses federated credentials and is the preferred method. | |
| − | On campus, there are 2 wireless networks | + | * '''VirginiaTech''': for guests and devices that cannot use the authentication method of '''eduroam'''. |
| − | + | Any remotely modern/complete Linux or Unix system will be able to connect to eduroam without any issues. | |
| − | + | Because '''eduroam''''s credentials are federated, it means that a VT user is able to automatically connect to the Internet at participating institutions. The eduroam-US site provides a [https://www.eduroam.us/technical_overview technical overview] of the authentication system. | |
==General Connection Information== | ==General Connection Information== | ||
===eduroam=== | ===eduroam=== | ||
| − | The following settings are recommended for connecting to the | + | The following settings are recommended for connecting to the eduroam network: |
* '''SSID:''' eduroam | * '''SSID:''' eduroam | ||
* '''EAP:''' PEAP | * '''EAP:''' PEAP | ||
* '''Phase 2:''' MSCHAPv2 | * '''Phase 2:''' MSCHAPv2 | ||
| − | * '''Root CA:''' | + | * '''Root CA:''' "USERTrust RSA Certification Authority" or pin the certificate (see below) |
* '''Server Name:''' eduroam.nis.vt.edu | * '''Server Name:''' eduroam.nis.vt.edu | ||
* '''Identity:''' pid@vt.edu (So if your PID was "hokiebird", hokiebird@vt.edu) | * '''Identity:''' pid@vt.edu (So if your PID was "hokiebird", hokiebird@vt.edu) | ||
| Line 25: | Line 25: | ||
The certificate presented by the RADIUS server is chained as such: | The certificate presented by the RADIUS server is chained as such: | ||
| − | * | + | * USERTrust RSA Certification Authority |
| − | ** | + | ** InCommon RSA Server CA |
| − | + | *** eduroam.nis.vt.edu | |
| − | |||
Below is where to obtain each of these, along with some metadata. The filenames are arbitrary, but will be used for the rest of this article. For every certificate (''especially'' the root, the signature chain helps with the rest), consider where you are obtaining it from and how much trust that you are getting what you think you are. You will probably want the PEM formatted certificate, if you have the option. | Below is where to obtain each of these, along with some metadata. The filenames are arbitrary, but will be used for the rest of this article. For every certificate (''especially'' the root, the signature chain helps with the rest), consider where you are obtaining it from and how much trust that you are getting what you think you are. You will probably want the PEM formatted certificate, if you have the option. | ||
| − | ==== | + | ====USERTrust RSA Certification Authority==== |
| − | ''Filename:'' | + | ''Filename:'' USERTrust_RSA_Certification_Authority.pem |
| − | ''Subject:'' | + | ''Subject:'' C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority |
| − | This is a common root CA and should have shipped with your OS. It is likely located in <code>/etc/ssl/certs/ | + | This is a common root CA and should have shipped with your OS. It is likely located in <code>/etc/ssl/certs/USERTrust_RSA_Certification_Authority.pem</code>. Note that if you follow the Authority Information Access of the intermediate certificate, it may direct you to a URL which points to a different version of this certficate, which is cross signed by AddTrust and expired in May 2020. The one in your cert store is self-signed and expires in 2038. You want the one from your cert store. |
| − | ==== | + | ====InCommon RSA Server CA==== |
| − | ''Filename:'' | + | ''Filename:'' InCommonRSAServerCA_2.pem |
| − | ''Subject:'' C = | + | ''Subject:'' C = US, ST = MI, L = Ann Arbor, O = Internet2, OU = InCommon, CN = InCommon RSA Server CA |
| − | This is an intermediate certificate | + | This is an intermediate certificate issued to InCommon. You can get it directly from InCommon [http://crt.usertrust.com/InCommonRSAServerCA_2.crt here]. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
====eduroam.nis.vt.edu==== | ====eduroam.nis.vt.edu==== | ||
| − | ''Filename:'' eduroam.nis.vt.edu. | + | ''Filename:'' eduroam.nis.vt.edu.pem |
| − | ''Subject:'' C = US, ST = Virginia, L = Blacksburg, O = Virginia Polytechnic Institute and State University, CN = eduroam.nis.vt.edu | + | ''Subject:'' C = US, postalCode = 24061, ST = Virginia, L = Blacksburg, street = 800 Washington St. SW, O = Virginia Polytechnic Institute and State University, OU = Secure Identity Services, CN = eduroam.nis.vt.edu |
| − | This can be obtained from the [https:// | + | This can be obtained from the [https://certs.it.vt.edu/search VT Certificate Manager]. This requires PID login. Search for "eduroam.nis.vt.edu". Grab the certificate most recently issued. |
===Validating the certificate=== | ===Validating the certificate=== | ||
| Line 69: | Line 60: | ||
<li> Obtain ''all'' certificates in the chain ''in PEM format'' </li> | <li> Obtain ''all'' certificates in the chain ''in PEM format'' </li> | ||
<li> Concatenate the non-leaf certificates in to a single file: </li> | <li> Concatenate the non-leaf certificates in to a single file: </li> | ||
| − | <pre>$ cat | + | <pre>$ cat USERTrust_RSA_Certification_Authority.pem InCommonRSAServerCA_2.pem > ca.pem</pre> |
<li> Verify the certificates are signed correctly </li> | <li> Verify the certificates are signed correctly </li> | ||
| − | <pre>$ openssl verify -verbose -purpose sslserver -CAfile ca.pem eduroam.nis.vt.edu. | + | <pre>$ openssl verify -verbose -purpose sslserver -CAfile ca.pem eduroam.nis.vt.edu.pem |
| − | eduroam.nis.vt.edu. | + | eduroam.nis.vt.edu.pem: OK</pre> |
<li> For at least the root and leaf certificates, verify the subject (compare to above) </li> | <li> For at least the root and leaf certificates, verify the subject (compare to above) </li> | ||
<pre>$ openssl x509 -in file_of_cert_you_want_to_check -noout -subject</pre> | <pre>$ openssl x509 -in file_of_cert_you_want_to_check -noout -subject</pre> | ||
| Line 83: | Line 74: | ||
Validate the certificate (see above) then generate the sha256 hash: | Validate the certificate (see above) then generate the sha256 hash: | ||
| − | $ openssl x509 -in | + | $ openssl x509 -in eduroam.nis.vt.edu.crt -outform der | sha256sum |
9b5163a3360f07b2dce2fd1e958c541687cf4c5360bb8adc87fa821c1c969910 - | 9b5163a3360f07b2dce2fd1e958c541687cf4c5360bb8adc87fa821c1c969910 - | ||
It is recommended that you perform these steps yourself rather than trusting the certificate hash presented in the configurations below. | It is recommended that you perform these steps yourself rather than trusting the certificate hash presented in the configurations below. | ||
| − | '''Note:''' As we are pinning the certificate instead of relying on a PKI, when NI&S rotates the certificates being used (at least every | + | '''Note:''' As we are pinning the certificate instead of relying on a PKI, when NI&S rotates the certificates being used (at least every year), the configuration will need to be updated to match the new certificate. |
| + | |||
| + | ===Getting your network password hash=== | ||
| + | MSCHAPv2 verifies the NT4 hash of your password, not the password itself. This means knowing the hash of the password is sufficient to connect to authenticate. Depending on the client, you may be able to store the hash in your config instead of the password. To reiterate, '''this hash is just as sensitive as your password'''. The hash is less human memorable, though, and does act as a deterrent to shoulder-surfing. | ||
| + | |||
| + | To derive the password hash, you can: | ||
| + | <pre> | ||
| + | printf 'YOUR-NETW-ORKP-SSWD' \ | ||
| + | | iconv -f ASCII -t UTF-16LE \ | ||
| + | | openssl dgst -md4 \ | ||
| + | | cut -d ' ' -f 2 | ||
| + | </pre> | ||
| + | |||
| + | If you are using OpenSSL 3, you will need to specify the legacy provider: | ||
| + | <pre> | ||
| + | | openssl dgst -md4 -provider legacy \ | ||
| + | </pre> | ||
===A Word of Caution=== | ===A Word of Caution=== | ||
Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic. | Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic. | ||
| − | We encourage you to take precautions against network eavesdropping and mischief (on the | + | We encourage you to take precautions against network eavesdropping and mischief (on the eduroam network, and in general). Potential countermeasures that one might want to employ include using [https://www.eff.org/HTTPS-EVERYWHERE HTTPS when connecting to sites], using a [https://www.computing.vt.edu/content/virtual-private-network VPN], or using the [https://www.torproject.org/ Tor Browser Bundle]. |
For general tips on improving your security while using the network, consider reading the EFF's [https://ssd.eff.org/ Surveillance Self-Defense] tips, reading [https://www.hokieprivacy.org/ Hokie Privacy], and/or contacting the [https://security.vt.edu/ Virginia Tech Information Security Office]. | For general tips on improving your security while using the network, consider reading the EFF's [https://ssd.eff.org/ Surveillance Self-Defense] tips, reading [https://www.hokieprivacy.org/ Hokie Privacy], and/or contacting the [https://security.vt.edu/ Virginia Tech Information Security Office]. | ||
| Line 99: | Line 106: | ||
==NetworkManager Instructions== | ==NetworkManager Instructions== | ||
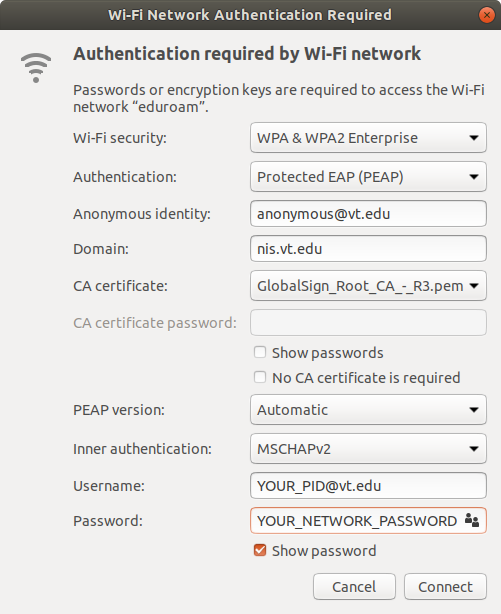
| − | + | In the list of wireless networks, select "eduroam". Set the following options: | |
| − | * | + | |
| − | * | + | * Wi-Fi security: WPA & WPA2 Enterprise |
| − | * | + | * Authentication: Protected EAP (PEAP) |
| − | * | + | * Anonymous identity: anonymous@vt.edu |
| − | * | + | * Domain: nis.vt.edu |
| + | * CA certificate: Select <code>/path/to/USERTrust_RSA_Certification_Authority.pem</code> via the file picker | ||
| + | * PEAP version: Automatic | ||
| + | * Inner authentication: MSCHAPv2 | ||
| + | * Username: PID@vt.edu | ||
| + | * Password: YOUR_NETWORK_PASSWORD | ||
| + | |||
| + | [[File:Nm settings.png]] | ||
==wpa_supplicant Instructions== | ==wpa_supplicant Instructions== | ||
| Line 124: | Line 138: | ||
phase2="auth=MSCHAPV2" | phase2="auth=MSCHAPV2" | ||
anonymous_identity="anonymous@vt.edu" | anonymous_identity="anonymous@vt.edu" | ||
| − | # | + | # if you prefer to pin the certificate, follow the instructions above to generate a hash |
| − | ca_cert="hash://server/sha256/ | + | ca_cert="hash://server/sha256/0000111122223333444455556666777788889999aaaabbbbccccddddeeeeffff" |
| − | # | + | # if you prefer to dynamically validate the certificate by its cryptographic attributes |
| − | domain_match=" | + | ca_cert="/path/to/USERTrust_RSA_Certification_Authority.pem" |
| − | identity=" | + | domain_match="eduroam.nis.vt.edu" |
| − | password=" | + | identity="PID@vt.edu" |
| + | password="YOUR_NETWORK_PASSWORD" | ||
} | } | ||
| Line 137: | Line 152: | ||
$ sudo dhcpcd wlan0 | $ sudo dhcpcd wlan0 | ||
| − | Alternate config options, besides domain_match | + | Alternate config options, besides domain_match are as follows (obviously not correct): |
subject_match="/C=US/ST=CA/L=San Francisco/CN=Test AS/emailAddress=as@example.com" | subject_match="/C=US/ST=CA/L=San Francisco/CN=Test AS/emailAddress=as@example.com" | ||
| − | domain_suffix_match=" | + | domain_suffix_match="nis.vt.edu" |
| + | |||
| + | More thorough documentation is available at [https://w1.fi/cgit/hostap/plain/wpa_supplicant/wpa_supplicant.conf] | ||
| + | |||
| + | ===OpenBSD Instructions=== | ||
| + | Since the [[OpenBSD]] network stack doesn't support 802.1x authentication, wpa_supplicant is needed to connect. wpa_supplicant on OpenBSD is different from its Linux counterpart in that it is only capable of 802.1x authentication and nothing more. First, install wpa_supplicant from ports if it is not already installed. After that, add just the <code>network={ .. }</code> portion of the above configuration to <code>/etc/wpa_supplicant.conf</code>. The wpa_supplicant service can be enabled with (where iwm0 is your wireless interface): | ||
| − | + | $ rcctl enable wpa_supplicant | |
| + | $ rcctl set wpa_supplicant flags -c /etc/wpa_supplicant.conf -s -D openbsd -i iwm0 | ||
| + | $ rcctl start wpa_supplicant | ||
| + | |||
| + | Finally, connect to the network with (again, replacing iwm0 with your wireless interface): | ||
| + | |||
| + | $ ifconfig iwm0 join eduroam wpa wpaakms 802.1x up | ||
| + | $ dhclient iwm0 | ||
| + | $ ifconfig iwm0 inet6 autoconf | ||
==netctl Instructions== | ==netctl Instructions== | ||
| Line 165: | Line 193: | ||
'anonymous_identity="anonymous@vt.edu"' | 'anonymous_identity="anonymous@vt.edu"' | ||
'ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"' | 'ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"' | ||
| − | 'domain_match=" | + | 'domain_match="eduroam.nis.vt.edu"' |
'identity="YourPidHere@vt.edu"' | 'identity="YourPidHere@vt.edu"' | ||
'password="YourNetworkPasswordHere"' | 'password="YourNetworkPasswordHere"' | ||
| Line 193: | Line 221: | ||
Name = eduroam | Name = eduroam | ||
EAP = peap | EAP = peap | ||
| − | CACertFile = /etc/ssl/certs/ | + | CACertFile = /etc/ssl/certs/USERTrust_RSA_Certification_Authority.pem |
| + | DomainMatch = eduroam.nis.vt.edu | ||
AnonymousIdentity = anonymous@vt.edu | AnonymousIdentity = anonymous@vt.edu | ||
Phase2 = MSCHAPV2 | Phase2 = MSCHAPV2 | ||
Identity = PID@vt.edu | Identity = PID@vt.edu | ||
Passphrase = NETWORKPASSWORD | Passphrase = NETWORKPASSWORD | ||
| + | </pre> | ||
| + | |||
| + | ==iwd Instructions== | ||
| + | This is a sample configuration, usually located at something like <code>/var/lib/iwd/eduroam.8021x</code>. For details, read <code>iwd.network(5)</code>. | ||
| + | |||
| + | <pre> | ||
| + | [Security] | ||
| + | EAP-Method = PEAP | ||
| + | EAP-Identity = anonymous@vt.edu | ||
| + | EAP-PEAP-CACert = embed:USERTrust_RSA_Certification_Authority | ||
| + | EAP-PEAP-ServerDomainMask = eduroam.nis.vt.edu | ||
| + | EAP-PEAP-Phase2-Method = MSCHAPV2 | ||
| + | EAP-PEAP-Phase2-Identity = PID@vt.edu | ||
| + | EAP-PEAP-Phase2-Password-Hash = 8846f7eaee8fb117ad06bdd830b7586c | ||
| + | |||
| + | [@pem@USERTrust_RSA_Certification_Authority] | ||
| + | -----BEGIN CERTIFICATE----- | ||
| + | MIIF3jCCA8agAwIBAgIQAf1tMPyjylGoG7xkDjUDLTANBgkqhkiG9w0BAQwFADCB | ||
| + | iDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0pl | ||
| + | cnNleSBDaXR5MR4wHAYDVQQKExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNV | ||
| + | BAMTJVVTRVJUcnVzdCBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTAw | ||
| + | MjAxMDAwMDAwWhcNMzgwMTE4MjM1OTU5WjCBiDELMAkGA1UEBhMCVVMxEzARBgNV | ||
| + | BAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0plcnNleSBDaXR5MR4wHAYDVQQKExVU | ||
| + | aGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNVBAMTJVVTRVJUcnVzdCBSU0EgQ2Vy | ||
| + | dGlmaWNhdGlvbiBBdXRob3JpdHkwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIK | ||
| + | AoICAQCAEmUXNg7D2wiz0KxXDXbtzSfTTK1Qg2HiqiBNCS1kCdzOiZ/MPans9s/B | ||
| + | 3PHTsdZ7NygRK0faOca8Ohm0X6a9fZ2jY0K2dvKpOyuR+OJv0OwWIJAJPuLodMkY | ||
| + | tJHUYmTbf6MG8YgYapAiPLz+E/CHFHv25B+O1ORRxhFnRghRy4YUVD+8M/5+bJz/ | ||
| + | Fp0YvVGONaanZshyZ9shZrHUm3gDwFA66Mzw3LyeTP6vBZY1H1dat//O+T23LLb2 | ||
| + | VN3I5xI6Ta5MirdcmrS3ID3KfyI0rn47aGYBROcBTkZTmzNg95S+UzeQc0PzMsNT | ||
| + | 79uq/nROacdrjGCT3sTHDN/hMq7MkztReJVni+49Vv4M0GkPGw/zJSZrM233bkf6 | ||
| + | c0Plfg6lZrEpfDKEY1WJxA3Bk1QwGROs0303p+tdOmw1XNtB1xLaqUkL39iAigmT | ||
| + | Yo61Zs8liM2EuLE/pDkP2QKe6xJMlXzzawWpXhaDzLhn4ugTncxbgtNMs+1b/97l | ||
| + | c6wjOy0AvzVVdAlJ2ElYGn+SNuZRkg7zJn0cTRe8yexDJtC/QV9AqURE9JnnV4ee | ||
| + | UB9XVKg+/XRjL7FQZQnmWEIuQxpMtPAlR1n6BB6T1CZGSlCBst6+eLf8ZxXhyVeE | ||
| + | Hg9j1uliutZfVS7qXMYoCAQlObgOK6nyTJccBz8NUvXt7y+CDwIDAQABo0IwQDAd | ||
| + | BgNVHQ4EFgQUU3m/WqorSs9UgOHYm8Cd8rIDZsswDgYDVR0PAQH/BAQDAgEGMA8G | ||
| + | A1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEMBQADggIBAFzUfA3P9wF9QZllDHPF | ||
| + | Up/L+M+ZBn8b2kMVn54CVVeWFPFSPCeHlCjtHzoBN6J2/FNQwISbxmtOuowhT6KO | ||
| + | VWKR82kV2LyI48SqC/3vqOlLVSoGIG1VeCkZ7l8wXEskEVX/JJpuXior7gtNn3/3 | ||
| + | ATiUFJVDBwn7YKnuHKsSjKCaXqeYalltiz8I+8jRRa8YFWSQEg9zKC7F4iRO/Fjs | ||
| + | 8PRF/iKz6y+O0tlFYQXBl2+odnKPi4w2r78NBc5xjeambx9spnFixdjQg3IM8WcR | ||
| + | iQycE0xyNN+81XHfqnHd4blsjDwSXWXavVcStkNr/+XeTWYRUc+ZruwXtuhxkYze | ||
| + | Sf7dNXGiFSeUHM9h4ya7b6NnJSFd5t0dCy5oGzuCr+yDZ4XUmFF0sbmZgIn/f3gZ | ||
| + | XHlKYC6SQK5MNyosycdiyA5d9zZbyuAlJQG03RoHnHcAP9Dc1ew91Pq7P8yF1m9/ | ||
| + | qS3fuQL39ZeatTXaw2ewh0qpKJ4jjv9cJ2vhsE/zB+4ALtRZh8tSQZXq9EfX7mRB | ||
| + | VXyNWQKV3WKdwrnuWih0hKWbt5DHDAff9Yk2dDLWKMGwsAvgnEzDHNb842m1R0aB | ||
| + | L6KCq9NjRHDEjf8tM7qtj3u1cIiuPhnPQCjY/MiQu12ZIvVS5ljFH4gxQ+6IHdfG | ||
| + | jjxDah2nGN59PRbxYvnKkKj9 | ||
| + | -----END CERTIFICATE----- | ||
</pre> | </pre> | ||
| Line 209: | Line 288: | ||
Steps: | Steps: | ||
| − | * | + | * Navigate to the list of Wi-Fi networks. |
| − | * | + | * "Forget" any existing entries for eduroam. |
* From the "WiFi networks" listing, click on eduroam. | * From the "WiFi networks" listing, click on eduroam. | ||
* Choose PEAP as the EAP method and MSCHAPv2 as the phase two authentication mechanism. | * Choose PEAP as the EAP method and MSCHAPv2 as the phase two authentication mechanism. | ||
| + | * For the CA certificate, select "Use system certificates". Optionally, import the root CA from above, and select that instead for better security. | ||
| + | * For the domain, enter ```eduroam.nis.vt.edu``` | ||
* Enter your pid@vt.edu for the identity | * Enter your pid@vt.edu for the identity | ||
* Enter "anonymous@vt.edu" for the anonymous identity | * Enter "anonymous@vt.edu" for the anonymous identity | ||
| Line 218: | Line 299: | ||
* Press "Connect". | * Press "Connect". | ||
| − | + | NOTE: Older versions of Android do not allow not verifying the server certificate. Setting both the root CA and the domain are essential for protecting your credentials. Although older versions will get you connected, use at your own risk. | |
==Frequently Asked Questions== | ==Frequently Asked Questions== | ||
===Is eduroam free?=== | ===Is eduroam free?=== | ||
| − | + | eduroam at Virginia Tech is free for: | |
| − | * VT affiliates with | + | * VT affiliates with wireless entitlements (includes students) access and network passwords |
* Users at other participating institutions | * Users at other participating institutions | ||
===Why is eduroam the preferred SSID?=== | ===Why is eduroam the preferred SSID?=== | ||
Using eduroam has several advantages: | Using eduroam has several advantages: | ||
| − | * | + | * The unencrypted portion of your authentication optionally identifies you as "anonymous@vt.edu" rather than revealing your PID |
* You have access to seamless roaming if you ever travel to another participating college campus | * You have access to seamless roaming if you ever travel to another participating college campus | ||
* The anonymous identity feature separates RADIUS authentication logs from the network access provider's logs | * The anonymous identity feature separates RADIUS authentication logs from the network access provider's logs | ||
| − | + | ===Does eduroam support EAP-TLS?=== | |
| + | Currently, the Virginia Tech eduroam RADIUS servers are not configured for EAP-TLS. | ||
==References== | ==References== | ||
| Line 243: | Line 325: | ||
[[Category:Howtos]] | [[Category:Howtos]] | ||
[[Category:Campus computing resources]] | [[Category:Campus computing resources]] | ||
| + | [[Category:Needs restoration]] | ||
Latest revision as of 14:00, 28 June 2023
On campus, there are 2 wireless networks:
- eduroam: uses federated credentials and is the preferred method.
- VirginiaTech: for guests and devices that cannot use the authentication method of eduroam.
Any remotely modern/complete Linux or Unix system will be able to connect to eduroam without any issues.
Because eduroam's credentials are federated, it means that a VT user is able to automatically connect to the Internet at participating institutions. The eduroam-US site provides a technical overview of the authentication system.
Contents
General Connection Information
eduroam
The following settings are recommended for connecting to the eduroam network:
- SSID: eduroam
- EAP: PEAP
- Phase 2: MSCHAPv2
- Root CA: "USERTrust RSA Certification Authority" or pin the certificate (see below)
- Server Name: eduroam.nis.vt.edu
- Identity: pid@vt.edu (So if your PID was "hokiebird", hokiebird@vt.edu)
- Anonymous Identity: anonymous@vt.edu
- Password: Your Network Password
Regardless of what software you use to establish your connection, you must first set your remote (network) passphrase by going to my.vt.edu→Settings→Change Network Password.
Obtaining the Certificate Chain
The certificate presented by the RADIUS server is chained as such:
- USERTrust RSA Certification Authority
- InCommon RSA Server CA
- eduroam.nis.vt.edu
- InCommon RSA Server CA
Below is where to obtain each of these, along with some metadata. The filenames are arbitrary, but will be used for the rest of this article. For every certificate (especially the root, the signature chain helps with the rest), consider where you are obtaining it from and how much trust that you are getting what you think you are. You will probably want the PEM formatted certificate, if you have the option.
USERTrust RSA Certification Authority
Filename: USERTrust_RSA_Certification_Authority.pem
Subject: C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
This is a common root CA and should have shipped with your OS. It is likely located in /etc/ssl/certs/USERTrust_RSA_Certification_Authority.pem. Note that if you follow the Authority Information Access of the intermediate certificate, it may direct you to a URL which points to a different version of this certficate, which is cross signed by AddTrust and expired in May 2020. The one in your cert store is self-signed and expires in 2038. You want the one from your cert store.
InCommon RSA Server CA
Filename: InCommonRSAServerCA_2.pem
Subject: C = US, ST = MI, L = Ann Arbor, O = Internet2, OU = InCommon, CN = InCommon RSA Server CA
This is an intermediate certificate issued to InCommon. You can get it directly from InCommon here.
eduroam.nis.vt.edu
Filename: eduroam.nis.vt.edu.pem
Subject: C = US, postalCode = 24061, ST = Virginia, L = Blacksburg, street = 800 Washington St. SW, O = Virginia Polytechnic Institute and State University, OU = Secure Identity Services, CN = eduroam.nis.vt.edu
This can be obtained from the VT Certificate Manager. This requires PID login. Search for "eduroam.nis.vt.edu". Grab the certificate most recently issued.
Validating the certificate
- Obtain all certificates in the chain in PEM format
- Concatenate the non-leaf certificates in to a single file:
- Verify the certificates are signed correctly
- For at least the root and leaf certificates, verify the subject (compare to above)
$ cat USERTrust_RSA_Certification_Authority.pem InCommonRSAServerCA_2.pem > ca.pem
$ openssl verify -verbose -purpose sslserver -CAfile ca.pem eduroam.nis.vt.edu.pem eduroam.nis.vt.edu.pem: OK
$ openssl x509 -in file_of_cert_you_want_to_check -noout -subject
Certificate Pinning
Due to vulnerabilities in the MSCHAPv2 protocol that allow the protocol to be cracked quickly with a 100% success rate[1], it is absolutely critical that the RADIUS server certificate be validated properly before attempting authentication. Where possible, we opt for the highest level of verification of the certificate: manually pinning the hash of the certificate we expect to be presented. The canonical form of the hash used by many network managers is the SHA256 hash of the DER encoding of the certificate.
Validate the certificate (see above) then generate the sha256 hash:
$ openssl x509 -in eduroam.nis.vt.edu.crt -outform der | sha256sum 9b5163a3360f07b2dce2fd1e958c541687cf4c5360bb8adc87fa821c1c969910 -
It is recommended that you perform these steps yourself rather than trusting the certificate hash presented in the configurations below.
Note: As we are pinning the certificate instead of relying on a PKI, when NI&S rotates the certificates being used (at least every year), the configuration will need to be updated to match the new certificate.
Getting your network password hash
MSCHAPv2 verifies the NT4 hash of your password, not the password itself. This means knowing the hash of the password is sufficient to connect to authenticate. Depending on the client, you may be able to store the hash in your config instead of the password. To reiterate, this hash is just as sensitive as your password. The hash is less human memorable, though, and does act as a deterrent to shoulder-surfing.
To derive the password hash, you can:
printf 'YOUR-NETW-ORKP-SSWD' \ | iconv -f ASCII -t UTF-16LE \ | openssl dgst -md4 \ | cut -d ' ' -f 2
If you are using OpenSSL 3, you will need to specify the legacy provider:
| openssl dgst -md4 -provider legacy \
A Word of Caution
Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic.
We encourage you to take precautions against network eavesdropping and mischief (on the eduroam network, and in general). Potential countermeasures that one might want to employ include using HTTPS when connecting to sites, using a VPN, or using the Tor Browser Bundle.
For general tips on improving your security while using the network, consider reading the EFF's Surveillance Self-Defense tips, reading Hokie Privacy, and/or contacting the Virginia Tech Information Security Office.
NetworkManager Instructions
In the list of wireless networks, select "eduroam". Set the following options:
- Wi-Fi security: WPA & WPA2 Enterprise
- Authentication: Protected EAP (PEAP)
- Anonymous identity: anonymous@vt.edu
- Domain: nis.vt.edu
- CA certificate: Select
/path/to/USERTrust_RSA_Certification_Authority.pemvia the file picker - PEAP version: Automatic
- Inner authentication: MSCHAPv2
- Username: PID@vt.edu
- Password: YOUR_NETWORK_PASSWORD
wpa_supplicant Instructions
wpa_supplicant is a cross-platform supplicant which implements IEEE 802.1x/WPA and is used in many Linux/UNIX distributions.
In order to connect to the eduroam network, add the following to /etc/wpa_supplicant/eduroam.conf modifying the identity and password to reflect your PID and Network Password:
ctrl_interface=DIR=/run/wpa_supplicant GROUP=wheel
update_config=1
fast_reauth=1
ap_scan=1
network={
ssid="eduroam"
proto=RSN
key_mgmt=WPA-EAP
eap=PEAP
phase2="auth=MSCHAPV2"
anonymous_identity="anonymous@vt.edu"
# if you prefer to pin the certificate, follow the instructions above to generate a hash
ca_cert="hash://server/sha256/0000111122223333444455556666777788889999aaaabbbbccccddddeeeeffff"
# if you prefer to dynamically validate the certificate by its cryptographic attributes
ca_cert="/path/to/USERTrust_RSA_Certification_Authority.pem"
domain_match="eduroam.nis.vt.edu"
identity="PID@vt.edu"
password="YOUR_NETWORK_PASSWORD"
}
You can then connect to the network by running (where wlan0 is your wireless interface):
$ sudo wpa_supplicant -B -i wlan0 -c /etc/wpa_supplicant/eduroam.conf $ sudo dhcpcd wlan0
Alternate config options, besides domain_match are as follows (obviously not correct):
subject_match="/C=US/ST=CA/L=San Francisco/CN=Test AS/emailAddress=as@example.com" domain_suffix_match="nis.vt.edu"
More thorough documentation is available at [2]
OpenBSD Instructions
Since the OpenBSD network stack doesn't support 802.1x authentication, wpa_supplicant is needed to connect. wpa_supplicant on OpenBSD is different from its Linux counterpart in that it is only capable of 802.1x authentication and nothing more. First, install wpa_supplicant from ports if it is not already installed. After that, add just the network={ .. } portion of the above configuration to /etc/wpa_supplicant.conf. The wpa_supplicant service can be enabled with (where iwm0 is your wireless interface):
$ rcctl enable wpa_supplicant $ rcctl set wpa_supplicant flags -c /etc/wpa_supplicant.conf -s -D openbsd -i iwm0 $ rcctl start wpa_supplicant
Finally, connect to the network with (again, replacing iwm0 with your wireless interface):
$ ifconfig iwm0 join eduroam wpa wpaakms 802.1x up $ dhclient iwm0 $ ifconfig iwm0 inet6 autoconf
netctl Instructions
netctl is a network manager which is native to the ArchLinux distribution. netctl makes use of wpa_supplicant under the hood, and so the configuration is similar.
Put the following configuration in /etc/netctl/eduroam with your proper PID and Network Password. Further, this assumes that your wireless network device is wlan0, which you might have to change to match your system. The ca_cert line pins the server certificate and can be generated/validated using the mechanism described above.
Description='Federated Educational Wifi Network'
Interface=wlan0
Connection=wireless
Security=wpa-configsection
IP=dhcp
IP6=stateless
WPAConfigSection=(
'ssid="eduroam"'
'proto=RSN'
'key_mgmt=WPA-EAP'
'eap=PEAP'
'phase2="auth=MSCHAPV2"'
'anonymous_identity="anonymous@vt.edu"'
'ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"'
'domain_match="eduroam.nis.vt.edu"'
'identity="YourPidHere@vt.edu"'
'password="YourNetworkPasswordHere"'
)
The ConfigSection (as per the netctl.profile manpage) is just what you would put in a wpa_supplicant config. Again, note that the domain_match is less secure than ca_cert, but better than not checking at all.
Ensure that this file is owned by root and only readable by root:
$ sudo chown root:root /etc/netctl/eduroam $ sudo chmod 600 /etc/netctl/eduroam
You can then start the connection using standard netctl methods:
$ sudo netctl start eduroam
connman Instructions
This config should be useable with connman. Replace Passphrase and Identity with your Network password and PID@vt.edu, respectively.
[global] Name = eduroam Description = Optionally put something descriptive here. [service_wifi_3c15c2e29584_656475726f616d_managed_ieee8021x] Type = wifi Name = eduroam EAP = peap CACertFile = /etc/ssl/certs/USERTrust_RSA_Certification_Authority.pem DomainMatch = eduroam.nis.vt.edu AnonymousIdentity = anonymous@vt.edu Phase2 = MSCHAPV2 Identity = PID@vt.edu Passphrase = NETWORKPASSWORD
iwd Instructions
This is a sample configuration, usually located at something like /var/lib/iwd/eduroam.8021x. For details, read iwd.network(5).
[Security] EAP-Method = PEAP EAP-Identity = anonymous@vt.edu EAP-PEAP-CACert = embed:USERTrust_RSA_Certification_Authority EAP-PEAP-ServerDomainMask = eduroam.nis.vt.edu EAP-PEAP-Phase2-Method = MSCHAPV2 EAP-PEAP-Phase2-Identity = PID@vt.edu EAP-PEAP-Phase2-Password-Hash = 8846f7eaee8fb117ad06bdd830b7586c [@pem@USERTrust_RSA_Certification_Authority] -----BEGIN CERTIFICATE----- MIIF3jCCA8agAwIBAgIQAf1tMPyjylGoG7xkDjUDLTANBgkqhkiG9w0BAQwFADCB iDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0pl cnNleSBDaXR5MR4wHAYDVQQKExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNV BAMTJVVTRVJUcnVzdCBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTAw MjAxMDAwMDAwWhcNMzgwMTE4MjM1OTU5WjCBiDELMAkGA1UEBhMCVVMxEzARBgNV BAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0plcnNleSBDaXR5MR4wHAYDVQQKExVU aGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNVBAMTJVVTRVJUcnVzdCBSU0EgQ2Vy dGlmaWNhdGlvbiBBdXRob3JpdHkwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIK AoICAQCAEmUXNg7D2wiz0KxXDXbtzSfTTK1Qg2HiqiBNCS1kCdzOiZ/MPans9s/B 3PHTsdZ7NygRK0faOca8Ohm0X6a9fZ2jY0K2dvKpOyuR+OJv0OwWIJAJPuLodMkY tJHUYmTbf6MG8YgYapAiPLz+E/CHFHv25B+O1ORRxhFnRghRy4YUVD+8M/5+bJz/ Fp0YvVGONaanZshyZ9shZrHUm3gDwFA66Mzw3LyeTP6vBZY1H1dat//O+T23LLb2 VN3I5xI6Ta5MirdcmrS3ID3KfyI0rn47aGYBROcBTkZTmzNg95S+UzeQc0PzMsNT 79uq/nROacdrjGCT3sTHDN/hMq7MkztReJVni+49Vv4M0GkPGw/zJSZrM233bkf6 c0Plfg6lZrEpfDKEY1WJxA3Bk1QwGROs0303p+tdOmw1XNtB1xLaqUkL39iAigmT Yo61Zs8liM2EuLE/pDkP2QKe6xJMlXzzawWpXhaDzLhn4ugTncxbgtNMs+1b/97l c6wjOy0AvzVVdAlJ2ElYGn+SNuZRkg7zJn0cTRe8yexDJtC/QV9AqURE9JnnV4ee UB9XVKg+/XRjL7FQZQnmWEIuQxpMtPAlR1n6BB6T1CZGSlCBst6+eLf8ZxXhyVeE Hg9j1uliutZfVS7qXMYoCAQlObgOK6nyTJccBz8NUvXt7y+CDwIDAQABo0IwQDAd BgNVHQ4EFgQUU3m/WqorSs9UgOHYm8Cd8rIDZsswDgYDVR0PAQH/BAQDAgEGMA8G A1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEMBQADggIBAFzUfA3P9wF9QZllDHPF Up/L+M+ZBn8b2kMVn54CVVeWFPFSPCeHlCjtHzoBN6J2/FNQwISbxmtOuowhT6KO VWKR82kV2LyI48SqC/3vqOlLVSoGIG1VeCkZ7l8wXEskEVX/JJpuXior7gtNn3/3 ATiUFJVDBwn7YKnuHKsSjKCaXqeYalltiz8I+8jRRa8YFWSQEg9zKC7F4iRO/Fjs 8PRF/iKz6y+O0tlFYQXBl2+odnKPi4w2r78NBc5xjeambx9spnFixdjQg3IM8WcR iQycE0xyNN+81XHfqnHd4blsjDwSXWXavVcStkNr/+XeTWYRUc+ZruwXtuhxkYze Sf7dNXGiFSeUHM9h4ya7b6NnJSFd5t0dCy5oGzuCr+yDZ4XUmFF0sbmZgIn/f3gZ XHlKYC6SQK5MNyosycdiyA5d9zZbyuAlJQG03RoHnHcAP9Dc1ew91Pq7P8yF1m9/ qS3fuQL39ZeatTXaw2ewh0qpKJ4jjv9cJ2vhsE/zB+4ALtRZh8tSQZXq9EfX7mRB VXyNWQKV3WKdwrnuWih0hKWbt5DHDAff9Yk2dDLWKMGwsAvgnEzDHNb842m1R0aB L6KCq9NjRHDEjf8tM7qtj3u1cIiuPhnPQCjY/MiQu12ZIvVS5ljFH4gxQ+6IHdfG jjxDah2nGN59PRbxYvnKkKj9 -----END CERTIFICATE-----
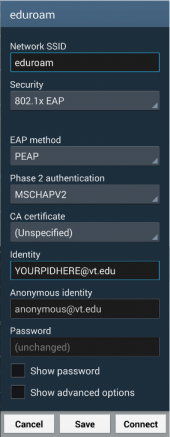
Android Instructions
A sample configuration is available to the right, but as this configuration is currently lacking CA certificate validation, we do not at this time recommend connecting to the network.
The Identity needs to be modified to match your PID@vt.edu, and your Network Password needs to be entered in the Password field.
Steps:
- Navigate to the list of Wi-Fi networks.
- "Forget" any existing entries for eduroam.
- From the "WiFi networks" listing, click on eduroam.
- Choose PEAP as the EAP method and MSCHAPv2 as the phase two authentication mechanism.
- For the CA certificate, select "Use system certificates". Optionally, import the root CA from above, and select that instead for better security.
- For the domain, enter ```eduroam.nis.vt.edu```
- Enter your pid@vt.edu for the identity
- Enter "anonymous@vt.edu" for the anonymous identity
- Enter your Network Password for the password
- Press "Connect".
NOTE: Older versions of Android do not allow not verifying the server certificate. Setting both the root CA and the domain are essential for protecting your credentials. Although older versions will get you connected, use at your own risk.
Frequently Asked Questions
Is eduroam free?
eduroam at Virginia Tech is free for:
- VT affiliates with wireless entitlements (includes students) access and network passwords
- Users at other participating institutions
Why is eduroam the preferred SSID?
Using eduroam has several advantages:
- The unencrypted portion of your authentication optionally identifies you as "anonymous@vt.edu" rather than revealing your PID
- You have access to seamless roaming if you ever travel to another participating college campus
- The anonymous identity feature separates RADIUS authentication logs from the network access provider's logs
Does eduroam support EAP-TLS?
Currently, the Virginia Tech eduroam RADIUS servers are not configured for EAP-TLS.