Difference between revisions of "Virginia Tech Wifi"
imported>Waldrep (→NetworkManager Instructions) |
imported>Pew |
||
| Line 257: | Line 257: | ||
[[Category:Howtos]] | [[Category:Howtos]] | ||
[[Category:Campus computing resources]] | [[Category:Campus computing resources]] | ||
| + | [[Category:Needs restoration]] | ||
Revision as of 03:55, 3 January 2018
On campus, there are 2 wireless networks. Eduroam is the preferred method, which uses PEAP-MSCHAPv2 to authenticate to the RADIUS server, while the second SSID, VirginiaTech, provides a captive-portal and allows for guest account creation.
As of January 2015 the preferred method of wireless access at Virginia Tech is through the Eduroam network. Eduroam is a secure wireless access service that was developed for the use of research and educational institutions. One of the advantages of the Eduroam network is that you will be able to connect to the Internet at any participating institution using your Virginia Tech credentials. The Eduroam-US site provides a technical overview of how the network authenticates you to the Virginia Tech RADIUS servers.
Contents
General Connection Information
eduroam
The following settings are recommended for connecting to the Eduroam network:
- SSID: eduroam
- EAP: PEAP
- Phase 2: MSCHAPv2
- Root CA: GlobalSign Root CA - R3 or pin the certificate (see below)
- Server Name: eduroam.nis.vt.edu
- Identity: pid@vt.edu (So if your PID was "hokiebird", hokiebird@vt.edu)
- Anonymous Identity: anonymous@vt.edu
- Password: Your Network Password
Regardless of what software you use to establish your connection, you must first set your remote (network) passphrase by going to my.vt.edu→Settings→Change Network Password.
Obtaining the Certificate Chain
The certificate presented by the RADIUS server is chained as such:
- GlobalSign Root CA - R3
- Trusted Root CA SHA256 G2
- Virginia Tech Global Qualified Server CA
- eduroam.nis.vt.edu
- Virginia Tech Global Qualified Server CA
- Trusted Root CA SHA256 G2
Below is where to obtain each of these, along with some metadata. The filenames are arbitrary, but will be used for the rest of this article. For every certificate (especially the root, the signature chain helps with the rest), consider where you are obtaining it from and how much trust that you are getting what you think you are. You will probably want the PEM formatted certificate, if you have the option.
GlobalSign Root CA - R3
Filename: GlobalSign_Root_CA_-_R3.pem
Subject: OU = GlobalSign Root CA - R3, O = GlobalSign, CN = GlobalSign
This is a common root CA and should have shipped with your OS. It is likely located in /etc/ssl/certs/GlobalSign_Root_CA_-_R3.pem. If you are unable to locate it in your OS, you can get it directly from GlobalSign. (This page seems to not be loading correctly at the moment. Here is the parent page.)
Trusted Root CA SHA256 G2
Filename: TrustedRootCASHA256G2.pem
Subject: C = BE, OU = Trusted Root, O = GlobalSign nv-sa, CN = Trusted Root CA SHA256 G2
This is an intermediate certificate, again issued by GlobalSign. You can get it directly from GlobalSign here.
Virginia Tech Global Qualified Server CA
Filename: VirginiaTechGlobalQualifiedServerCA.pem
Subject: C = US, ST = Virginia, L = Blacksburg, OU = Global Qualified Server CA, O = Virginia Polytechnic Institute and State University, CN = Virginia Tech Global Qualified Server CA
This can be obtained from the Virginia Tech PKI website. This website is only available from VT IP addresses (including VPN). Although certificates higher in the chain are also provided here, the page does not support https. DO NOT get your root CA here.
eduroam.nis.vt.edu
Filename: eduroam.nis.vt.edu.crt
Subject: C = US, ST = Virginia, L = Blacksburg, O = Virginia Polytechnic Institute and State University, CN = eduroam.nis.vt.edu
This can be obtained from the VTCA Certificate Manager. This requires PID login. Search for "eduroam.nis.vt.edu". Note: As of 2017 June 19, there will be 2 results, due to some internal testing. Download the certificate with the serial 3699307517ED7E8B. The certificate with serial 7A083CC134D0303D is incorrect.
Validating the certificate
- Obtain all certificates in the chain in PEM format
- Concatenate the non-leaf certificates in to a single file:
- Verify the certificates are signed correctly
- For at least the root and leaf certificates, verify the subject (compare to above)
$ cat GlobalSign_Root_CA_-_R3.pem TrustedRootCASHA256G2.pem VirginiaTechGlobalQualifiedServerCA.pem >> ca.pem
$ openssl verify -verbose -purpose sslserver -CAfile ca.pem eduroam.nis.vt.edu.crt eduroam.nis.vt.edu.crt: OK
$ openssl x509 -in file_of_cert_you_want_to_check -noout -subject
Certificate Pinning
Due to vulnerabilities in the MSCHAPv2 protocol that allow the protocol to be cracked quickly with a 100% success rate[1], it is absolutely critical that the RADIUS server certificate be validated properly before attempting authentication. Where possible, we opt for the highest level of verification of the certificate: manually pinning the hash of the certificate we expect to be presented. The canonical form of the hash used by many network managers is the SHA256 hash of the DER encoding of the certificate.
Validate the certificate (see above) then generate the sha256 hash:
$ openssl x509 -in eduroam.nis.vt.edu.crt -outform der | sha256sum 9b5163a3360f07b2dce2fd1e958c541687cf4c5360bb8adc87fa821c1c969910 -
It is recommended that you perform these steps yourself rather than trusting the certificate hash presented in the configurations below.
Note: As we are pinning the certificate instead of relying on a PKI, when NI&S rotates the certificates being used (at least every 2 years), the configuration will need to be updated to match the new certificate.
A Word of Caution
Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic.
We encourage you to take precautions against network eavesdropping and mischief (on the Eduroam network, and in general). Potential countermeasures that one might want to employ include using HTTPS when connecting to sites, using a VPN, or using the Tor Browser Bundle.
For general tips on improving your security while using the network, consider reading the EFF's Surveillance Self-Defense tips, reading Hokie Privacy, and/or contacting the Virginia Tech Information Security Office.
NetworkManager Instructions
In the list of wireless networks, select "eduroam". Set the following options:
- Wi-Fi security: WPA & WPA2 Enterprise
- Authentication: Protected EAP (PEAP)
- Anonymous identity: anonymous@vt.edu
- CA certificate: Select
/path/to/GlobalSign_Root_CA_-_R3.pemvia the file picker - PEAP version: Automatic
- Inner authentication: MSCHAPv2
- Username: PID@vt.edu
- Password: YOUR_NETWORK_PASSWORD
NOTE: There does not appear to be a way to set the expected server name. This means that anyone with a certificate that chains back to the same root CA can setup a rouge AP taht ouwl successfully MitM traffic from a device using this configuration.
wpa_supplicant Instructions
wpa_supplicant is a cross-platform supplicant which implements IEEE 802.1x/WPA and is used in many Linux/UNIX distributions.
In order to connect to the eduroam network, add the following to /etc/wpa_supplicant/eduroam.conf modifying the identity and password to reflect your PID and Network Password:
ctrl_interface=DIR=/run/wpa_supplicant GROUP=wheel
update_config=1
fast_reauth=1
ap_scan=1
network={
ssid="eduroam"
proto=RSN
key_mgmt=WPA-EAP
eap=PEAP
phase2="auth=MSCHAPV2"
anonymous_identity="anonymous@vt.edu"
#THIS HASH IS OUT OF DATE, PLEASE FOLLOW INSTRUCTIONS ABOVE
# if you prefer to pin the certificate
ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"
# if you prefer to dynamically validate the certificate by its cryptographic attributes
ca_cert="/path/to/GlobalSign_Root_CA_-_R3.pem"
domain_match="eduroam.nis.vt.edu"
identity="YourPidHere@vt.edu"
password="YourNetworkPasswordHere"
}
You can then connect to the network by running (where wlan0 is your wireless interface):
$ sudo wpa_supplicant -B -i wlan0 -c /etc/wpa_supplicant/eduroam.conf $ sudo dhcpcd wlan0
Alternate config options, besides domain_match are as follows (obviously not correct):
subject_match="/C=US/ST=CA/L=San Francisco/CN=Test AS/emailAddress=as@example.com" domain_suffix_match="nis.vt.edu"
More thorough documentation is available at [2]
netctl Instructions
netctl is a network manager which is native to the ArchLinux distribution. netctl makes use of wpa_supplicant under the hood, and so the configuration is similar.
Put the following configuration in /etc/netctl/eduroam with your proper PID and Network Password. Further, this assumes that your wireless network device is wlan0, which you might have to change to match your system. The ca_cert line pins the server certificate and can be generated/validated using the mechanism described above.
Description='Federated Educational Wifi Network'
Interface=wlan0
Connection=wireless
Security=wpa-configsection
IP=dhcp
IP6=stateless
WPAConfigSection=(
'ssid="eduroam"'
'proto=RSN'
'key_mgmt=WPA-EAP'
'eap=PEAP'
'phase2="auth=MSCHAPV2"'
'anonymous_identity="anonymous@vt.edu"'
'ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"'
'domain_match="eduroam.nis.vt.edu"'
'identity="YourPidHere@vt.edu"'
'password="YourNetworkPasswordHere"'
)
The ConfigSection (as per the netctl.profile manpage) is just what you would put in a wpa_supplicant config. Again, note that the domain_match is less secure than ca_cert, but better than not checking at all.
Ensure that this file is owned by root and only readable by root:
$ sudo chown root:root /etc/netctl/eduroam $ sudo chmod 600 /etc/netctl/eduroam
You can then start the connection using standard netctl methods:
$ sudo netctl start eduroam
connman Instructions
This config should be useable with connman. Replace Passphrase and Identity with your Network password and PID@vt.edu, respectively.
[global] Name = eduroam Description = Optionally put something descriptive here. [service_wifi_3c15c2e29584_656475726f616d_managed_ieee8021x] Type = wifi Name = eduroam EAP = peap CACertFile = /etc/ssl/certs/GlobalSign_Root_CA_-_R3.pem DomainMatch = eduroam.nis.vt.edu AnonymousIdentity = anonymous@vt.edu Phase2 = MSCHAPV2 Identity = PID@vt.edu Passphrase = NETWORKPASSWORD
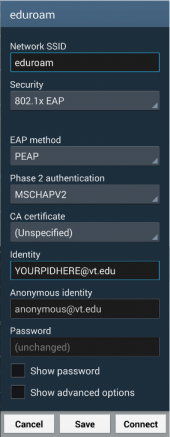
Android Instructions
A sample configuration is available to the right, but as this configuration is currently lacking CA certificate validation, we do not at this time recommend connecting to the network.
The Identity needs to be modified to match your PID@vt.edu, and your Network Password needs to be entered in the Password field.
Steps:
- From the home screen, press the menu button and choose "Settings"→"Wireless & networks"→"Wi-Fi settings".
- Remove any existing entries for eduroam.
- From the "WiFi networks" listing, click on eduroam.
- Choose PEAP as the EAP method and MSCHAPv2 as the phase two authentication mechanism.
- Enter your pid@vt.edu for the identity
- Enter "anonymous@vt.edu" for the anonymous identity
- Enter your Network Password for the password
- Press "Connect".
TODO: Android certificate validation
Quick and dirty options for validating the eduroam certificate, in order from least secure to most secure:
- Do not validate: you will get online, but consider your connection to be as secure as a public hotspot
- (Android 7.1+ only) Use system certificates: This will check to make sure the certificate chains back to some CA in the system cert store. This is significantly better than no validation, but still not very good. You may also need to specify a domain. If so, use "vt.edu"
- Download and import the GlobalSign Root CA: detailed instructions to come. Since you are still not checking the CN, it is only marginally better than using system certificates.
- Use the eduroam CAT tool: this will setup the whole wireless profile and use the correct CA and verify the CN. As such, it is the preferred method. Warning, it is ugly. If you have an existing "eduroam" profile, you will need to remove it. When it prompts for the username and password, use <YOUR-PID>@vt.edu and your network password. It relies on geolocation to prompt for the profile for the right school. You may need to go outside to get a good GPS signal. If it is able to do geo-ip (e.g., you are connected to the "VirginiaTech" SSID), it gets you close enough.
Frequently Asked Questions
Is eduroam free?
eduroam at Virginia Tech is free for:
- VT affiliates with wireless entitlements (includes students) access and network passwords
- Users at other participating institutions
Why is eduroam the preferred SSID?
Using eduroam has several advantages:
- The unencrypted portion of your authentication optionally identifies you as "anonymous@vt.edu" rather than revealing your PID
- You have access to seamless roaming if you ever travel to another participating college campus
- The anonymous identity feature separates RADIUS authentication logs from the network access provider's logs
Does eduroam support EAP-TLS?
Currently, the Virginia Tech eduroam RADIUS servers are not configured for EAP-TLS.