Difference between revisions of "Virginia Tech Wifi"
imported>Ram m (Add this page to the Campus computing resources Category) |
imported>Mjh (Added verifcation instructions) |
||
| Line 2: | Line 2: | ||
As of January 2015 the [https://www.computing.vt.edu/content/eduroam preferred method] of wireless access at Virginia Tech is through the [https://eduroam.org/ Eduroam] network. Eduroam is a secure wireless access service that was developed for the use of research and educational institutions. One of the advantages of the Eduroam network over the VT-Wireless network is that you will be able to connect to the Internet at any participating institution using your Virginia Tech credentials. The Eduroam-US site provides a [https://www.eduroam.us/technical_overview technical overview] of how the network authenticates you to the Virginia Tech RADIUS servers. | As of January 2015 the [https://www.computing.vt.edu/content/eduroam preferred method] of wireless access at Virginia Tech is through the [https://eduroam.org/ Eduroam] network. Eduroam is a secure wireless access service that was developed for the use of research and educational institutions. One of the advantages of the Eduroam network over the VT-Wireless network is that you will be able to connect to the Internet at any participating institution using your Virginia Tech credentials. The Eduroam-US site provides a [https://www.eduroam.us/technical_overview technical overview] of how the network authenticates you to the Virginia Tech RADIUS servers. | ||
| − | |||
| − | |||
==Connection Information== | ==Connection Information== | ||
| Line 16: | Line 14: | ||
* Password: [https://www.computing.vt.edu/kb/entry/3765 Your Network Password] | * Password: [https://www.computing.vt.edu/kb/entry/3765 Your Network Password] | ||
| − | ====Certificate Pinning | + | ===Legacy connections=== |
| + | It may be still possible to use older networks, but their use is deprecated in favor of eduroam and thus unsupported. | ||
| + | * [[Virginia Tech Wifi: VT-Wireless]] - VT-Wireless with PEAP-MSCHAPv2 (network password) | ||
| + | * [[EAP-TLS]] - VT-Wireless with EAP-TLS (netcerts) | ||
| + | |||
| + | ===Certificate Pinning=== | ||
Due to vulnerabilities in the MSCHAPv2 protocol that allow the protocol to be cracked quickly with a 100% success rate<ref>[https://www.cloudcracker.com/blog/2012/07/29/cracking-ms-chap-v2/]</ref>, it is ''absolutely critical'' that the RADIUS server certificate be validated properly before attempting authentication. Unfortunately, VT is in the process of deprecating a much stronger authentication method, [[EAP-TLS]], and as such, network certificates will no longer be an option. | Due to vulnerabilities in the MSCHAPv2 protocol that allow the protocol to be cracked quickly with a 100% success rate<ref>[https://www.cloudcracker.com/blog/2012/07/29/cracking-ms-chap-v2/]</ref>, it is ''absolutely critical'' that the RADIUS server certificate be validated properly before attempting authentication. Unfortunately, VT is in the process of deprecating a much stronger authentication method, [[EAP-TLS]], and as such, network certificates will no longer be an option. | ||
| Line 24: | Line 27: | ||
In order to generate the certificate hash, download the certificate by clicking the "Download" link on the [https://ash.eprov.seti.vt.edu/EJBCAWebRequest/certSearch?cmd=search&keyword=VT-Wireless Certificate Search for VT-Wireless] (Unfortunately this site is only available to Virginia Tech IPs) | In order to generate the certificate hash, download the certificate by clicking the "Download" link on the [https://ash.eprov.seti.vt.edu/EJBCAWebRequest/certSearch?cmd=search&keyword=VT-Wireless Certificate Search for VT-Wireless] (Unfortunately this site is only available to Virginia Tech IPs) | ||
| − | Validate that the downloaded certificate is in fact signed by the (Now Obsolete) [https://secure.hosting.vt.edu/www.pki.vt.edu/developer/rootca.html#globalserver Virginia Tech Global Server CA] chain. | + | Validate that the downloaded certificate is in fact signed by the (Now Obsolete) [https://secure.hosting.vt.edu/www.pki.vt.edu/developer/rootca.html#globalserver Virginia Tech Global Server CA] chain. You will first need to download ''all'' certificates in the "CA: Virginia_Tech_Global_Server_CA" chain and concatenate them. |
| − | + | $ cat GlobalSignRootCA.pem GlobalSignRootSignPartnersCA.pem VirginiaTechGlobalRootCA.pem VirginiaTechGlobalServerCA.pem >> ca.pem | |
| + | $ openssl verify -verbose -purpose sslserver -CAfile ca.pem VT-Wireless.cns.vt.edu.crt | ||
| + | VT-Wireless.cns.vt.edu.crt: OK | ||
Then generate the sha256 hash (in the directory where the certificate downloaded to): | Then generate the sha256 hash (in the directory where the certificate downloaded to): | ||
| Line 37: | Line 42: | ||
'''Note:''' As we are pinning the certificate instead of relying on a PKI, when CNS rotates the certificates being used, the configuration will need to be updated to match the new certificate. | '''Note:''' As we are pinning the certificate instead of relying on a PKI, when CNS rotates the certificates being used, the configuration will need to be updated to match the new certificate. | ||
| − | + | ===A Word of Caution=== | |
Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic. | Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic. | ||
We encourage you to take precautions against network eavesdropping and mischief (on the Eduroam network, and in general). Potential countermeasures that one might want to employ include using [https://www.eff.org/HTTPS-EVERYWHERE HTTPS when connecting to sites], using a [https://www.computing.vt.edu/content/virtual-private-network VPN], or using the [https://www.torproject.org/ Tor Browser Bundle]. | We encourage you to take precautions against network eavesdropping and mischief (on the Eduroam network, and in general). Potential countermeasures that one might want to employ include using [https://www.eff.org/HTTPS-EVERYWHERE HTTPS when connecting to sites], using a [https://www.computing.vt.edu/content/virtual-private-network VPN], or using the [https://www.torproject.org/ Tor Browser Bundle]. | ||
| − | For general tips on improving your security while using the network, consider | + | For general tips on improving your security while using the network, consider reading the EFF's [https://ssd.eff.org/ Surveillance Self-Defense] tips, reading [https://www.hokieprivacy.org/ Hokie Privacy], and/or contacting the [https://security.vt.edu/ Virginia Tech Information Security Office]. |
==Set Your Remote Access (Network) Passphrase== | ==Set Your Remote Access (Network) Passphrase== | ||
Revision as of 17:48, 6 February 2015
There are three wireless networks on campus. One network, called VT-Wireless, encrypts all traffic and is secured with EAP-TLS or PEAP-MSCHAPv2. A second network, CONNECTtoVT-Wireless, an unencrypted, captive portal wireless network designed to set up connecting to VT-Wireless without offering Internet access. Due to user issues faced during deployment, CONNECTtoVT-Wireless began offering captive portal access to VT users.
As of January 2015 the preferred method of wireless access at Virginia Tech is through the Eduroam network. Eduroam is a secure wireless access service that was developed for the use of research and educational institutions. One of the advantages of the Eduroam network over the VT-Wireless network is that you will be able to connect to the Internet at any participating institution using your Virginia Tech credentials. The Eduroam-US site provides a technical overview of how the network authenticates you to the Virginia Tech RADIUS servers.
Contents
Connection Information
eduroam
The following settings are recommended for connecting to the Eduroam network:
- SSID: eduroam
- EAP: PEAP
- Phase 2: MSCHAPv2
- Identity: pid@vt.edu (So if your PID was "hokiebird", hokiebird@vt.edu)
- Anonymous Identity: anonymous@vt.edu
- Password: Your Network Password
Legacy connections
It may be still possible to use older networks, but their use is deprecated in favor of eduroam and thus unsupported.
- Virginia Tech Wifi: VT-Wireless - VT-Wireless with PEAP-MSCHAPv2 (network password)
- EAP-TLS - VT-Wireless with EAP-TLS (netcerts)
Certificate Pinning
Due to vulnerabilities in the MSCHAPv2 protocol that allow the protocol to be cracked quickly with a 100% success rate[1], it is absolutely critical that the RADIUS server certificate be validated properly before attempting authentication. Unfortunately, VT is in the process of deprecating a much stronger authentication method, EAP-TLS, and as such, network certificates will no longer be an option.
Where possible, we opt for the highest level of verification of the certificate: manually pinning the hash of the certificate we expect to be presented. The canonical form of the hash used by many network managers is the SHA256 hash of the DER encoding of the certificate.
In order to generate the certificate hash, download the certificate by clicking the "Download" link on the Certificate Search for VT-Wireless (Unfortunately this site is only available to Virginia Tech IPs)
Validate that the downloaded certificate is in fact signed by the (Now Obsolete) Virginia Tech Global Server CA chain. You will first need to download all certificates in the "CA: Virginia_Tech_Global_Server_CA" chain and concatenate them.
$ cat GlobalSignRootCA.pem GlobalSignRootSignPartnersCA.pem VirginiaTechGlobalRootCA.pem VirginiaTechGlobalServerCA.pem >> ca.pem $ openssl verify -verbose -purpose sslserver -CAfile ca.pem VT-Wireless.cns.vt.edu.crt VT-Wireless.cns.vt.edu.crt: OK
Then generate the sha256 hash (in the directory where the certificate downloaded to):
$ openssl x509 -in VT-Wireless.cns.vt.edu.crt -outform der | sha256sum 216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a -
It is recommended that you perform these steps yourself rather than trusting the certificate hash presented in the configurations below.
Note: As we are pinning the certificate instead of relying on a PKI, when CNS rotates the certificates being used, the configuration will need to be updated to match the new certificate.
A Word of Caution
Although you can verify connection to the Virginia Tech RADIUS servers you must keep in mind that you are connecting to a network that you do not control. It is possible that there are network monitors in place which can record and potentially modify traffic.
We encourage you to take precautions against network eavesdropping and mischief (on the Eduroam network, and in general). Potential countermeasures that one might want to employ include using HTTPS when connecting to sites, using a VPN, or using the Tor Browser Bundle.
For general tips on improving your security while using the network, consider reading the EFF's Surveillance Self-Defense tips, reading Hokie Privacy, and/or contacting the Virginia Tech Information Security Office.
Set Your Remote Access (Network) Passphrase
Regardless of what software you use to establish your connection, you must first set your remote passphrase by going to my.vt.edu→Settings→Change Network Password.
NetworkManager
- In your wireless configuration program, select eduroam.
- Choose PEAP as the EAP type.
- Choose MSCHAPv2 as the authentication method.
- Use PID@vt.edu and network passphrase as your login credentials.
- Use anonymous@vt.edu as your Anonymous Identity
- TODO: Certificate verification (Warning, until certificate verification is added, it is not recommended that you use this method of accessing the network.)
wpa_supplicant
wpa_supplicant is a cross-platform supplicant which implements IEEE 802.1x/WPA and is used in many Linux/UNIX distributions.
In order to connect to the eduroam network, add the following to /etc/wpa_supplicant/eduroam.conf modifying the identity and password to reflect your PID and Network Password:
ctrl_interface=DIR=/run/wpa_supplicant GROUP=wheel
update_config=1
fast_reauth=1
ap_scan=1
network={
ssid="eduroam"
proto=RSN
key_mgmt=WPA-EAP
eap=PEAP
phase2="auth=MSCHAPV2"
anonymous_identity="anonymous@vt.edu"
ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"
identity="YourPidHere@vt.edu"
password="YourNetworkPasswordHere"
}
You can then connect to the network by running (where wlan0 is your wireless interface):
$ sudo wpa_supplicant -B -i wlan0 -c /etc/wpa_supplicant/eduroam.conf $ sudo dhcpcd wlan0
netctl
netctl is a network manager which is native to the ArchLinux distribution. netctl makes use of wpa_supplicant under the hood, and so the configuration is similar.
Put the following configuration in /etc/netctl/eduroam with your proper PID and Network Password. Further, this assumes that your wireless network device is wlan0, which you might have to change to match your system. The ca_cert line pins the server certificate and can be generated/validated using the mechanism described above.
Description='Federated Educational Wifi Network'
Interface=wlan0
Connection=wireless
Security=wpa-configsection
IP=dhcp
IP6=stateless
WPAConfigSection=(
'ssid="eduroam"'
'proto=RSN'
'key_mgmt=WPA-EAP'
'eap=PEAP'
'phase2="auth=MSCHAPV2"'
'anonymous_identity="anonymous@vt.edu"'
'ca_cert="hash://server/sha256/216c5f2568c6e84860b12535efe93500623ccee999306b84260f951bcbd57b1a"'
'identity="YourPidHere@vt.edu"'
'password="YourNetworkPasswordHere"'
)
Ensure that this file is owned by root and only readable by root:
$ sudo chown root:root /etc/netctl/eduroam $ sudo chmod 600 /etc/netctl/eduroam
You can then start the connection using standard netctl methods:
$ sudo netctl start eduroam
Android
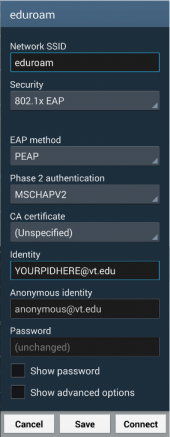
A sample configuration is available to the right, but as this configuration is currently lacking CA certificate validation, we do not at this time recommend connecting to the network.
The Identity needs to be modified to match your PID@vt.edu, and your Network Password needs to be entered in the Password field.
Steps:
- From the home screen, press the menu button and choose "Settings"→"Wireless & networks"→"Wi-Fi settings".
- Remove any existing entries for eduroam.
- From the "WiFi networks" listing, click on eduroam.
- Choose PEAP as the EAP method and MSCHAPv2 as the phase two authentication mechanism.
- Enter your pid@vt.edu for the identity
- Enter "anonymous@vt.edu" for the anonymous identity
- Enter your Network Password for the password
- Press "Connect".
TODO: Android certificate validation